This is staggering. We received that DNS lookup request on our DNS server.
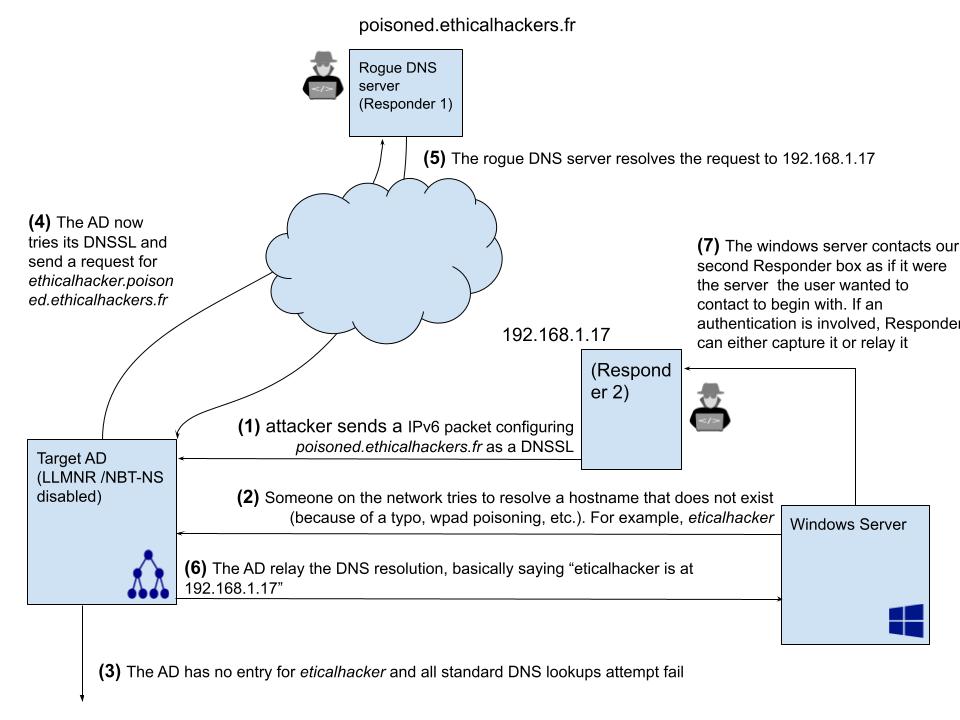
Let’s go all the way, setup a quick vps, and try to do the same thing with our own domain (ethicalhackers.fr), instead of a test DNS server.
My DNS entries:
poisoned.ethicalhackers.fr. NS satin.ethicalhackers.fr.
satin.ethicalhackers.fr. A 12.184.201.116
Now, if anyone tries to lookup for example test.poisoned.ethicalhackers.fr, they will relay the query to 12.184.201.116, which is our VPS public IP (don’t forget to open port 53 UDP there).
On 12.184.201.116, we start Responder.
To test that everything is set up properly, let’s induce a lookup to our domain.